Genetec Shares Data Privacy Best Practices for Physical Security Teams Ahead of Data Protection Day
As International Data Protection Day approaches on January 28, Genetec Inc., the global leader in enterprise physical security software, has released comprehensive recommendations to help organizations protect sensitive physical security data while maintaining effective security operations.
The Growing Challenge of Physical Security Data Management
Modern physical security systems generate enormous volumes of sensitive information, including video footage, access control records, and license plate data. This information plays an increasingly critical role in daily operations and investigations, creating significant management challenges for organizations.
Organizations now face mounting pressure to manage this data responsibly amid evolving privacy regulations, escalating cyber threats, and heightened public expectations around transparency and data handling practices.
A Call for Proactive Data Protection Strategies
"Physical security data can be highly sensitive, and protecting it requires more than basic safeguards or vague assurances," emphasized Mathieu Chevalier, Principal Security Architect at Genetec Inc. "Some approaches in the market treat data as an asset to be exploited or shared beyond its original purpose. That creates real privacy risks."
Chevalier further explained that organizations should expect clear limits on how their data is used, strong controls throughout its lifecycle, and technology designed to respect privacy by default rather than as an afterthought.
Essential Best Practices for Data Protection
International Data Protection Day serves as an important reminder that protecting personal data represents a shared and ongoing responsibility. For physical security teams, adopting clear strategies, resilient technologies, and trusted partnerships can help ensure privacy and security objectives remain aligned as risks and regulations continue to evolve.
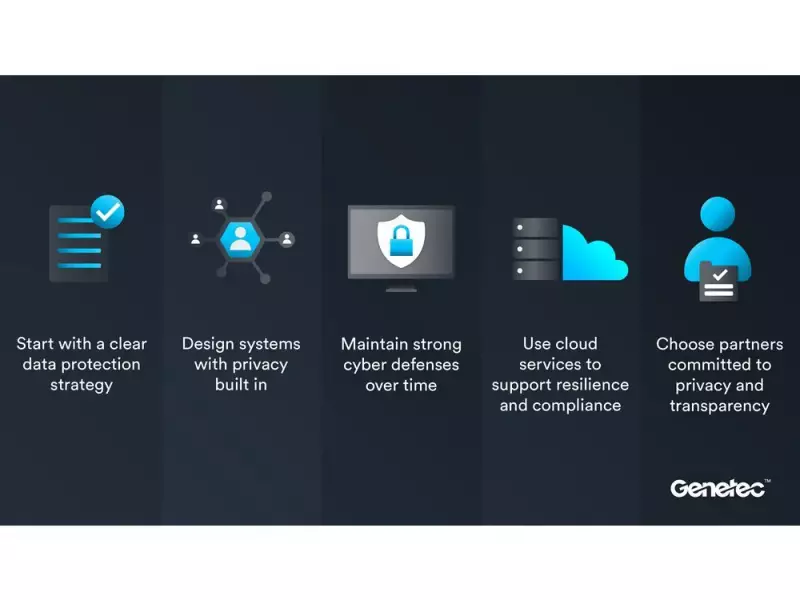
Genetec recommends the following best practices to help organizations strengthen data protection across their physical security systems:
Develop a Clear Data Protection Strategy
Organizations should regularly assess what data they collect, the purposes for collection, storage locations, retention periods, and access permissions. Documenting these practices helps reduce unnecessary data exposure, identify policy gaps, and support ongoing compliance as regulations continue to evolve.
Transparency around data handling practices also plays a crucial role in building trust with employees, customers, and the general public.
Implement Privacy-by-Design Principles
Privacy-by-design means limiting privacy risk not only through security controls but also through how personal data is collected, used, and governed. Organizations should apply purpose limitation and data minimization principles to ensure only the data required for defined security objectives is collected and retained.
Strong security measures, including encrypting data in transit and at rest, enforcing robust authentication protocols, and applying granular access controls, help reduce the risk of unauthorized access.
Privacy-enhancing technologies, such as automated anonymization and masking, further support transparency and help protect individuals' identities while preserving the operational value of security data.
The Path Forward for Security Teams
As physical security systems become increasingly sophisticated and data-intensive, organizations must prioritize both security effectiveness and privacy protection. The recommendations from Genetec provide a practical framework for security teams to navigate the complex landscape of data protection while maintaining operational efficiency.
By implementing these best practices, organizations can better safeguard sensitive information, comply with evolving regulations, and build greater trust with stakeholders who expect responsible data management from modern security operations.